With 15 million data records exposed in the third quarter of 2022, it is no surprise that most people consider security and privacy extinct qualities on the web.
But did you know there’s an effective way to ensure your personal data and online activity remains safe? The answer is in getting a VPN.
If you don’t know VPN meaning, it stands for a virtual private network. It creates a private tunnel between the users and the websites they visit. VPNs keep all prying eyes and snoopers at bay, including the government, ISPs, advertisers, hackers, etc. Continue scrolling to learn how VPNs protect your privacy and secure your data.
How Do VPNs Keep Your Data Secure?
VPNs encrypt the user’s online presence and prevent hackers and third parties from snooping. Without the key, the encryption cannot be deciphered.
Therefore, hackers or cyber criminals only get to see scrambled data that makes no sense. The key is only known by the VPN service you are using and your computer. Therefore, even your Internet service provider cannot track your online activity.
Although different VPNs utilize different encryption techniques, the process typically works in the following three stages:
- Boot up your VPN online to act as a secure tunnel between your Internet connection and computer. The tunnel is hidden from third parties, including your ISP.
- As soon as you enable VPN, your system will be on the VPN’s local network, and the IP address will be disguised.
- You can browse the web as you please because VPN will protect your data and privacy.

How Do VPNs Work?
VPNs hide IP addresses by redirecting them via a specially configured remote server, which the VPN host runs. Therefore, when you browse online using this service, the origin of data is one of the VPN’s servers.
Thanks to this, nobody can track your online activities and the websites you are visiting. Also, if someone did manage to get their hands on the data sent between your computer and the Internet, it would be gibberish.
So before you choose a comprehensive VPN service, ensure it can do the following things:
1. Encryption of logs
The VPN service you use mustn’t allow you to leave a trail of your browsing activities, such as cookies, search history, and Internet history.
Therefore, it is critical to encrypt the cookies so that third parties are prevented from viewing sensitive information like financial information, personal details, and other content that you may submit to the websites from time to time. In addition, VPNs stop data from being tracked back to you.
2. IP Address Encryption
Keeping IP addresses encrypted and hidden is one of the essential tasks of VPNs. This enables users to send and receive information online without anyone monitoring their online activities and browsing habits.
3. Multi-factor Authentication
VPNs verify people trying to log in through several authentications. For example, you might be asked to provide a password and then enter the code sent to your mobile number or email. Thanks to this, hackers find it extremely difficult to access a secure connection.
4. Kill Switch
In rare instances when the VPN connection suddenly drops, users’ secure connection will also take a hit. That’s why VPN providers include a feature called a kill switch that immediately detects sudden downtime and quits pre-selected programs. Therefore, there’s less risk of data exposure.
The Three Common Types Of VPNs You Must Know
Although there are several types of VPN, the following three are the most commonly used.
1. Site-to-Site VPNs
These typically provide a private network that disguises private intranets while enabling users to access each other’s resources. This type of VPN is useful for businesses operating from multiple locations, each with their LAN connected to a WAN. A site-to-site VPN is generally used in large-scale businesses and is considered the most effective way to secure communications across the company.
2. Remote Access VPNs
These connect the user to a remote server, and most individuals use this type of VPN. A remote access VPN can easily set up and securely encrypts browsing data, along with changing IP addresses to access geo-blocked content. However, this type of VPN is not the best for handling complex business needs.
3. Client-to-Provider VPNs
When using this form of VPN, users are not connected to the Internet through their ISP. Instead, they are connected directly through their VPN provider. That’s why the tunnel stage in the VPN journey is cut out.
The VPN does not need to create an encrypted tunnel but automatically encrypts the data before it reaches its final destination. The client-to-provider VPN is a common type of VPN, proving useful for public Wi-Fi network providers.
Thanks to this, third parties are prevented from accessing data and compromising network connections. Even ISPs are prevented from accessing data.
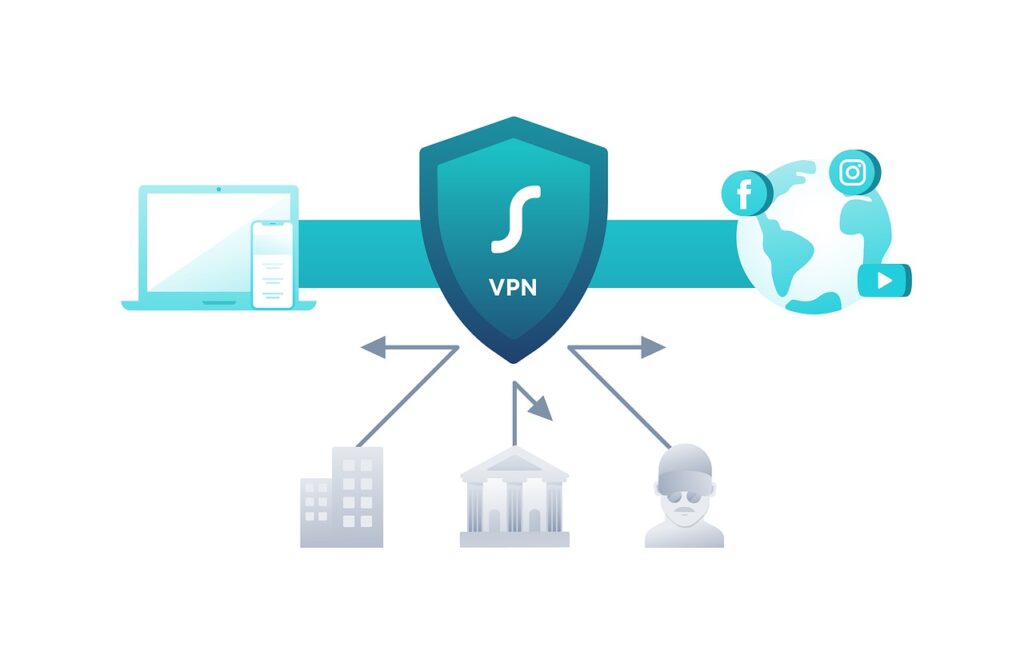
Besides Privacy Protection, How Else Does A VPN Benefit Users?
VPNs’ first and foremost function is to protect your privacy and keep your data safe. This is done through an encrypted tunnel that safeguards communication between the Internet and the user, along with IP address masking to keep online identity anonymous.
But this is not the only benefit you’ll enjoy with a VPN. Along with keeping your data safe online, VPNs allow users to enjoy geo-blocked content on the Internet. So, for example, if you want to watch a Netflix show or play a game unavailable in your country, you can use VPN.
All you need to do is change the server location, and then you can unlock the geo-restricted content. Furthermore, VPNs help overcome censorship obstacles you might face when you need to access confidential information.
Final Thoughts
Security and privacy online are not outdated concepts, but you must be vigilant to protect yourself. With a VPN, you can safeguard your personal and financial information and prevent ISPs, governments, and hackers from monitoring and tracking your browsing habits and online activities. So install a VPN today and browse the Internet with complete peace of mind.
Ella Marcotte
Latest posts by Ella Marcotte (see all)
- UA vs GA4: The 4 Big Differences You Need To Know - April 8, 2024
- Understanding The Role Of Control Valves In Industrial Automation - April 8, 2024
- How Automation Can Boost Your Business Outcomes - April 4, 2024




